Verification
Verifi.life for Government
Government departments use video conferencing for a wide range of purposes, facilitating communication and service delivery across various levels of governance. Here’s an overview of common uses and an analysis of which might be most vulnerable to impersonation fraud by cloned bots:
Diplomatic communications: This is perhaps the most critical area. A sophisticated AI bot impersonating a diplomat or high-ranking official could potentially manipulate international relations, leak sensitive information, or make unauthorized commitments.
Remote court proceedings: Bot impersonation in legal settings could lead to false testimonies, manipulated evidence, or compromised legal decisions.
Emergency management briefings: Impersonation during crisis situations could lead to misinformation, misdirection of resources, or panic if false information is disseminated.
Citizen services: Bots impersonating citizens could potentially access personal information, manipulate records, or obtain fraudulent documents.
Inter-agency meetings: Impersonation here could lead to unauthorized information sharing between departments, compromising sensitive operations or policies.
These areas are particularly vulnerable because:
- They often involve high-stakes decision-making with far-reaching consequences.
- There’s an inherent expectation of trust and authenticity in government communications.
- The information exchanged is often sensitive or classified.
- The remote nature of video conferencing removes some traditional security measures.
As government operations increasingly rely on digital platforms, including video conferencing, it’s crucial to balance the benefits of remote communication with robust security measures. The potential for AI-driven impersonation in government contexts presents significant national security risks, making it essential for government departments to stay at the forefront of cybersecurity practices and technological advancements in identity verification.
Try it free, no credit card required.
verifi works with these, and many other video platforms
reporting
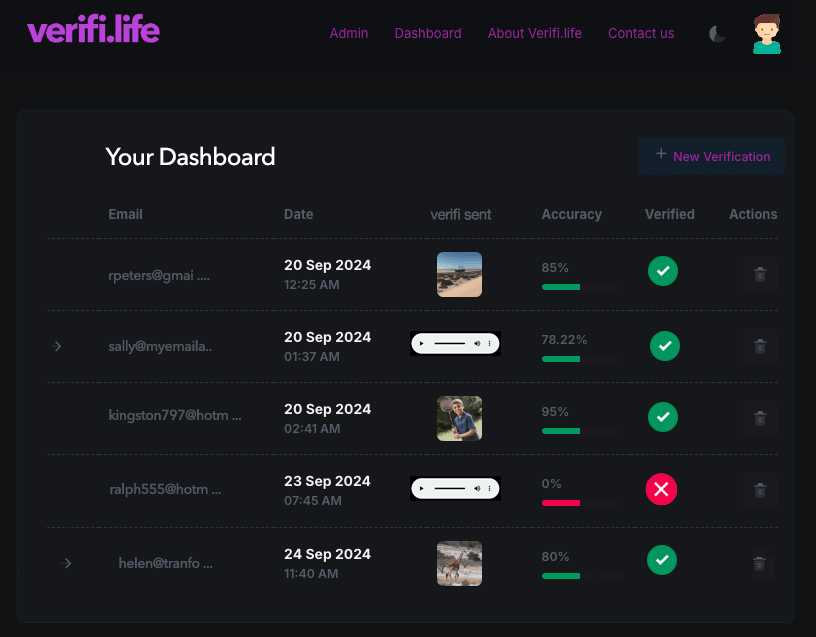
The record of every verifi.cation is stored in your account. Reports have a screen shot of the recipient you called together with all the relevant information you might need.

use it today
Simple to use.
Use verifi.life as an extension to your browser, or open it on a web page. It just takes a couple of clicks to get the assurance that the person you are talking to, is in fact, a person.
Try it free, no credit card required.