employee verification
Verifi.life for Remote Working
Employers with remote workers use video conferences in various ways to manage, collaborate with, and support their distributed workforce. Here’s an overview of common uses and an analysis of which might be most vulnerable to impersonation fraud by cloned bots:
Among these uses, the most troublesome in terms of potential fraud from impersonation by cloned bots are:
One-on-one performance reviews: This is perhaps the most vulnerable area. A sophisticated AI bot could potentially impersonate an employee, providing false information about performance, goals, or challenges. This could lead to misallocation of resources, unfair evaluations, or even fraudulent bonus allocations.
Technical support sessions: Bot impersonation here could lead to unauthorized access to company systems, data breaches, or the installation of malware under the guise of “fixing” issues.
Client presentations: If a bot impersonates a team member during a client meeting, it could potentially damage client relationships, make false commitments, or leak sensitive information.
Training sessions: Bots impersonating employees could manipulate training outcomes, leading to false records of completed training or misunderstanding of crucial company policies.
Project kickoffs: Impersonation at this stage could result in misassignment of tasks, miscommunication of project goals, or unauthorized access to project resources.
These areas are particularly vulnerable because:
- They often involve one-on-one or small group interactions where familiarity with all participants may be limited.
- They frequently deal with sensitive or confidential information.
- The remote nature of the work makes it harder to verify physical presence or identity.
- There’s often an expectation of trust in these professional contexts.
As remote work continues to be prevalent and AI technology advances, employers will need to balance the benefits of video conferencing with robust security measures to protect against sophisticated impersonation attempts. Regular training and updating of security protocols will be crucial in this evolving landscape.
Try it free, no credit card required.
verifi works with these, and many other video platforms
reporting
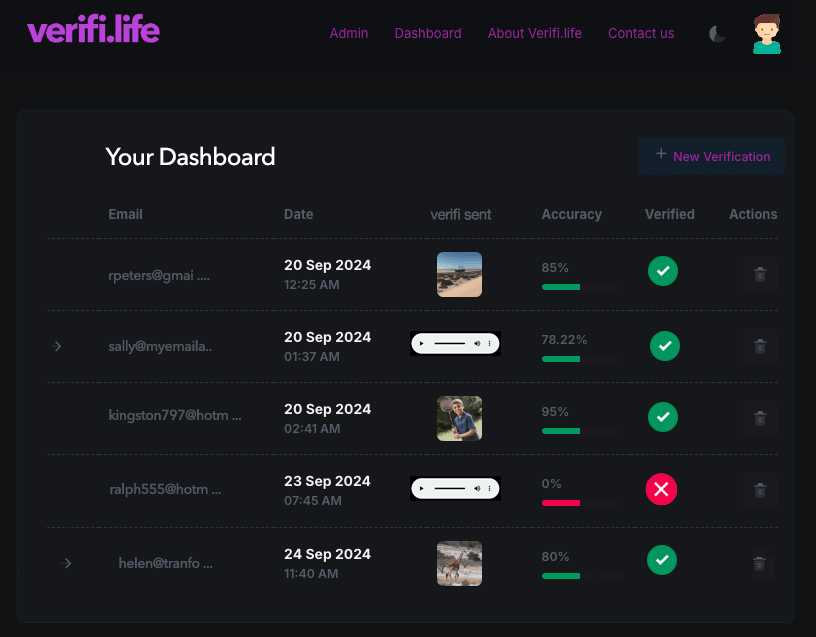
The record of every verifi.cation is stored in your account. Reports have a screen shot of the recipient you called together with all the relevant information you might need.

use it today
Simple to use.
Use verifi.life as an extension to your browser, or open it on a web page. It just takes a couple of clicks to get the assurance that the person you are talking to, is in fact, a person.
Try it free, no credit card required.











